bcc
BPF Compiler Collection (BCC)是基于eBPF的Linux内核分析、跟踪、网络监控工具。其源码存放于https://github.com/iovisor/bcc。
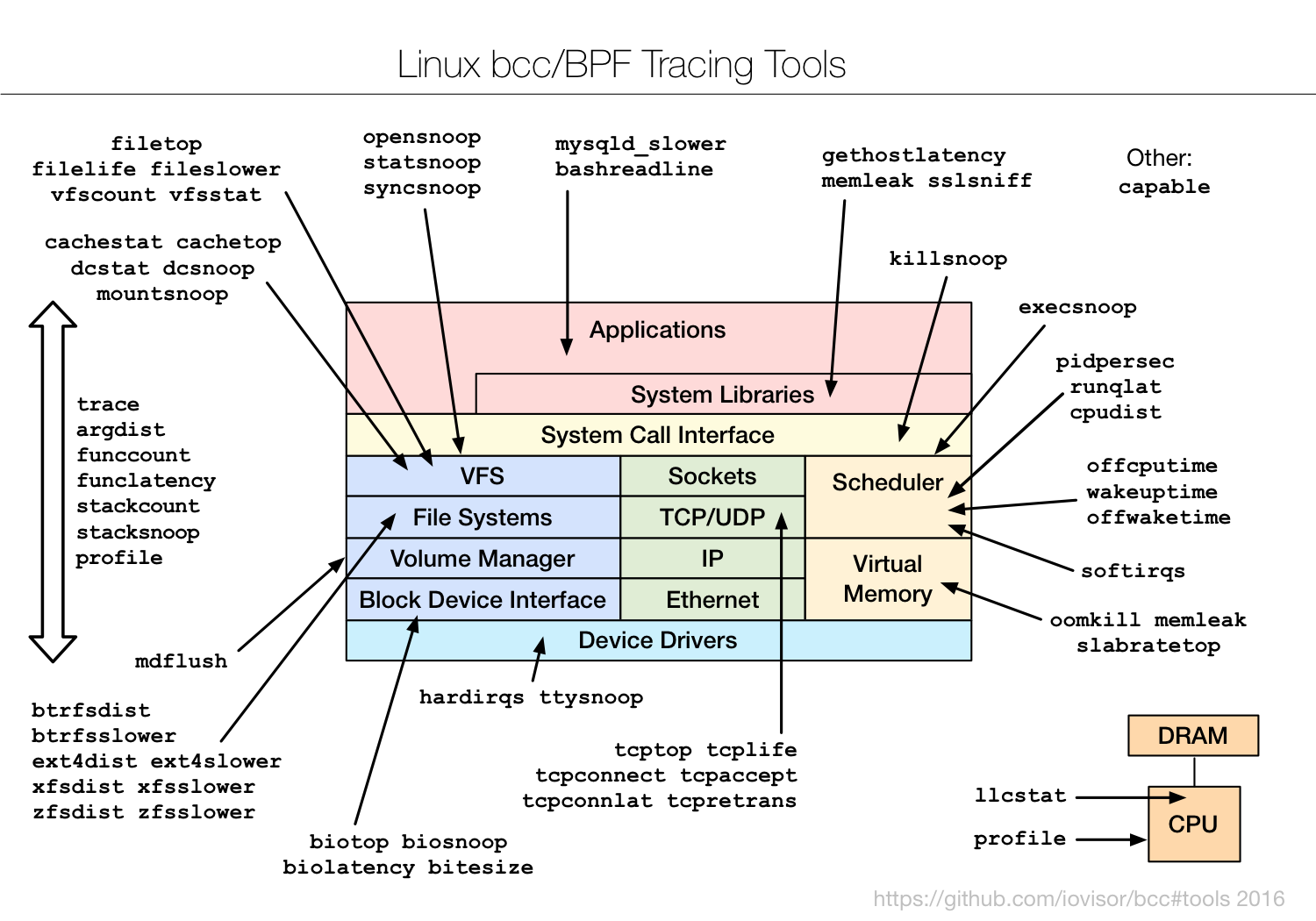
BCC包括一些列的工具
安装BCC
Ubuntu:
CentOS:
安装完成后,bcc工具会放到/usr/share/bcc/tools目录中
常用工具示例
capable
capable检查Linux进程的security capabilities:
tcpconnect
tcpconnect检查活跃的TCP连接,并输出源和目的地址:
tcptop
tcptop统计TCP发送和接受流量:
扩展工具
基于eBPF和bcc,可以很方便的扩展功能。bcc目前支持以下事件
kprobe__kernel_function_name(BPF.attach_kprobe())kretprobe__kernel_function_name(BPF.attach_kretprobe())TRACEPOINT_PROBE(category, event),支持的event列表参见/sys/kernel/debug/tracing/events/category/event/formatBPF.attach_uprobe()和BPF.attach_uretprobe()用户自定义探针(USDT)
USDT.enable_probe()
简单示例
使用BPF_PERF_OUTPUT
BPF_PERF_OUTPUT更多的示例参考https://github.com/iovisor/bcc/blob/master/docs/tutorial_bcc_python_developer.md。
用户自定义探针示例
参考文档
最后更新于